Security monitoring
Security monitoring refers to the automated and centralized process of detecting and analyzing indications of potential security threats so that appropriate action can then be taken against these cyber threats.
Security is critical for any business. With the increasing use of technology and digital processes, it is more important than ever to have a comprehensive security monitoring system in place. Unfortunately, traditional blocking measures (e.g. a firewall) and an adequate SIEM (Security Incident and Event Management System) are no longer sufficient to protect against hacker attacks. Security Monitoring offers you permanent monitoring of your IT infrastructure. In doing so, certain softwares (e.g. Splunk) make real-time visual correlations to identify malicious activity and real risks are prioritized so you can take immediate action.
Why Security Monitoring?
- Reduction of downtime in the network
- Initiation of measures against cyber threats
- Reduction of damage through fast and early attack detection
- Protection against internal and external threats
- Increasing the barriers for the attackers
- Saving of follow-up costs
Our approach
We attach great importance to adapting our service to customer needs and developing customized solutions. In doing so, we work closely with our customers to ensure they get exactly what they need. We ensure that the systems and data are protected at all times and that they can be responded to quickly in the event of an attack.
Use Case
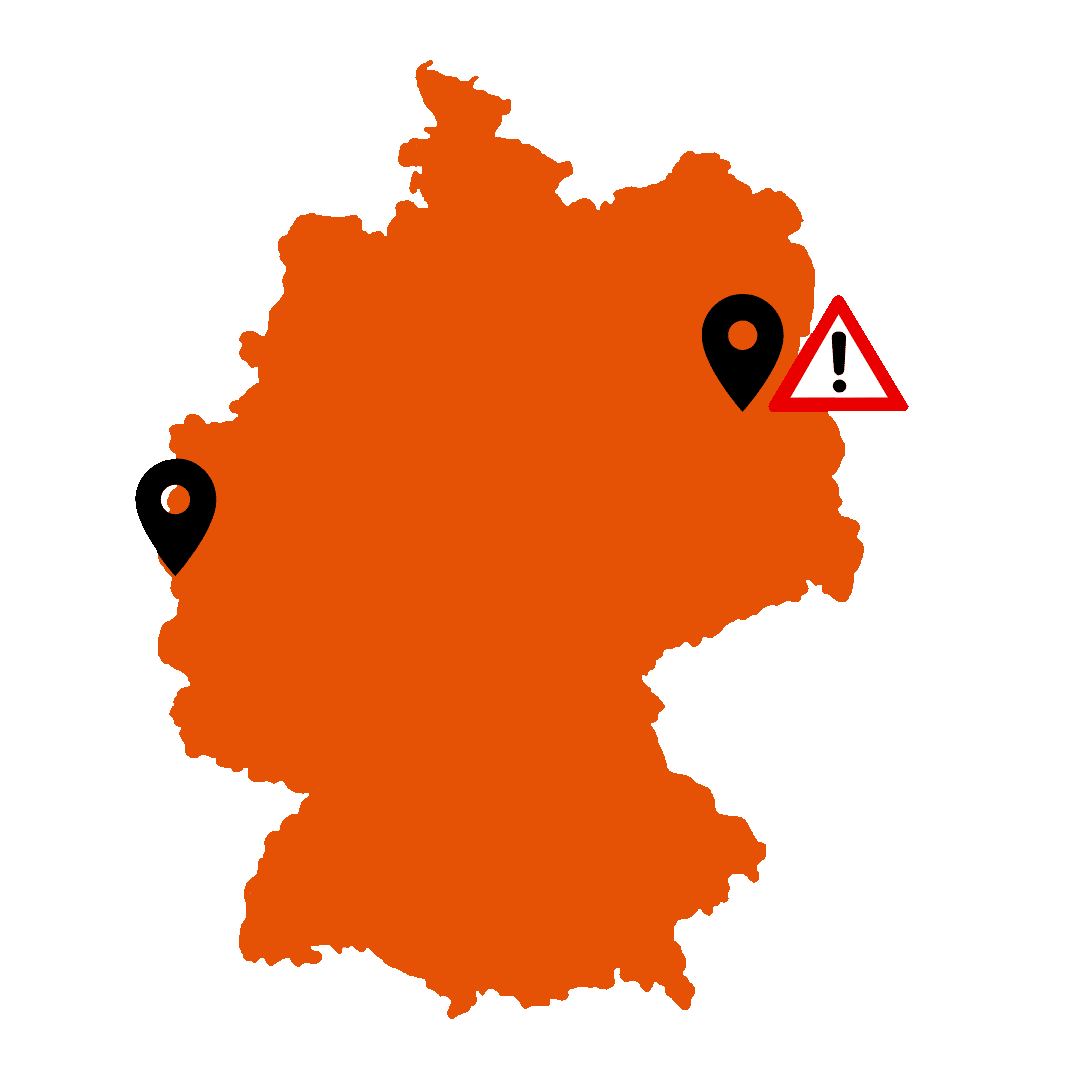
Imagine one of your employees (m,f,d) logs into your company’s internal wiki in Aachen. Everything is fine. However, the same employee logs in 10 minutes later in Berlin.
How can the employee get from Aachen to Berlin in 10 minutes? Usually it is not possible. A security monitoring tool like Splunk detects this potential security threat and raises the alarm immediately.
A first possible measure is to temporarily block the account and then contact the employee. This simple but very effective measure can massively reduce or almost completely prevent damage.